Contain ransomware
Contain ransomware outbreaks
Protect your business with multi-layered security
Ransomware Containment doesn’t replace your endpoint protection platforms (EPP) and endpoint detection and response (EDR) tools. It complements them. Rather than preventing ransomware from getting in, it stops any active attacks that do get through.
Limits operational impact
Outbreaks are identified and stopped at the source, limiting the impact on company-wide productivity.
Implements quickly
This agentless, cloud service does NOT install on endpoints or servers making for a hassle-free implementation.
Protects against financial loss
Immediate response and endpoint isolation stops system-wide data encryption reducing the risk of expensive recovery efforts, legal costs, and ransoms.
Works invisibly
With no local agents or server applications, you experience no impact on network, device, or application performance.
Reduces recovery time
An event report details the exact files infected that need restoration, saving valuable time.
Gives peace of mind
Protection against ransomware events that bypass perimeter defenses enable you to be more agile, and confident your business data remains safe.
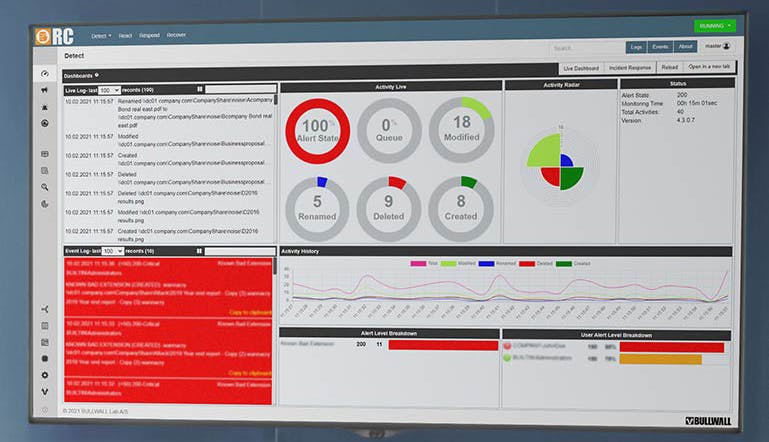
How Ransomware Containment works
Active Detection
Artificial intelligence (AI) and machine learning establish a baseline of file activity on your network. It monitors file changes constantly using heuristics and metadata to detect ransomware encryption the moment it starts. By monitoring file behavior, it detects both known and unknown ransomware variants.
Immediate Response
An automated containment protocol shuts down the infected endpoint the moment ransomware’s illegitimate encryption begins. Isolation methods used include disabling VPN, disabling NAC, disabling AD-user, and forced shutdown. Alerts are sent to designated security administrators.
Informed Recovery
Your security and recovery team can pull reporting that shows the exact files infected prior to the forced shutdown. This makes restoration from backup simple. And all attack details are captured in a history log for insight into affected files.
A comprehensive last line of protection from ransomware
See more about ransomware and cybersecurity
Is my business really at risk of a cyber-attack
Get added protection against ransomware
Frequently asked questions
Explore additional IT insights
Ransomware containment for a historical Massachusetts city
The City of Watertown completes its cybersecurity strategy by deploying RansomCare powered by BullWall, which stops, isolates and contains ransomware at the source.
Digital documents and managing the risks of ransomware
The risks of ransomware have skyrocketed as documents and data have gone digital like never before. Assess your data security profile here.
Medical Research and Development Company
A medical research company goes 100% cloud bolstering its security and cutting costs.